-
Noticias Feed
- EXPLORE
-
Páginas
-
Grupos
-
Eventos
-
Blogs
-
Marketplace
-
Foros
-
Juegos
Securing the Cyber Gates: Trends in the Identity and Access Management Landscape
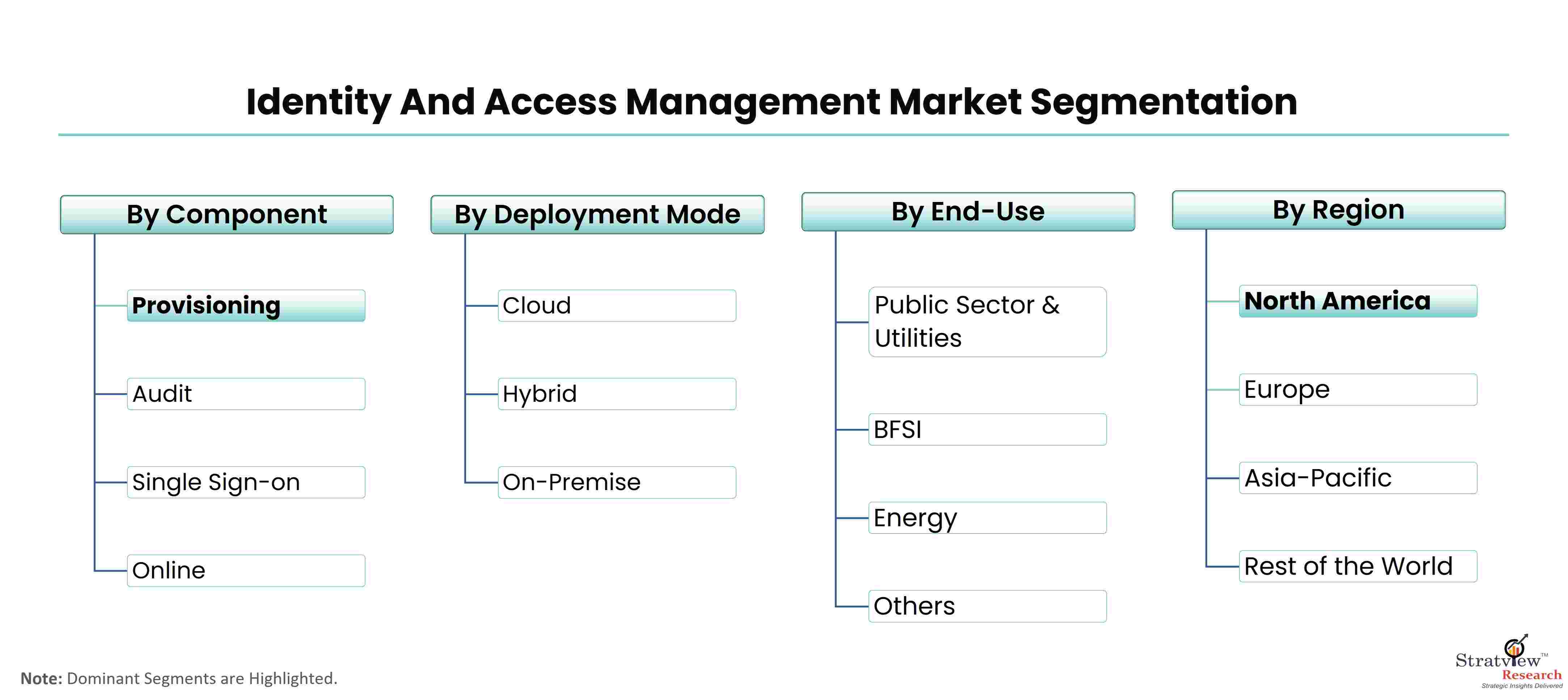
According to Stratview Research, the identity and access management market was estimated at USD 13.7 billion in 2022 and is likely to grow at a CAGR of 15.2% during 2023-2028 to reach USD 32.1 billion in 2028.
In the digital age, where data is both a prized asset and a potential vulnerability, the importance of securing the cyber gates cannot be overstated. Identity and Access Management (IAM) stands as the first line of defense, safeguarding sensitive information and digital assets from unauthorized access. This article explores the trends shaping the IAM landscape, highlighting the innovative strategies and technologies that are enhancing cybersecurity and fortifying the cyber gates against evolving threats.
IAM in the Age of Remote Work: The paradigm shift towards remote work has intensified the focus on IAM. Organizations are adopting IAM solutions that provide secure access to resources for employees working from diverse locations. The trend is towards a flexible yet robust IAM infrastructure that accommodates the dynamic nature of remote work.
Zero Trust Architecture: Zero Trust is no longer just a concept; it's a guiding principle in the IAM landscape. The Zero Trust model assumes that threats can come from both internal and external sources, requiring continuous verification of identities and devices. This trend emphasizes a holistic approach to security, treating every access attempt with skepticism until proven otherwise.
Biometric Authentication Evolution: Biometric authentication is undergoing a significant evolution, moving beyond fingerprints and facial recognition. Emerging trends include behavioral biometrics, voice recognition, and even continuous authentication methods. The aim is to provide more accurate and adaptive identification measures, enhancing security while ensuring a user-friendly experience.
Adaptive Access Policies: Static access policies are giving way to adaptive access policies that take into account various contextual factors. IAM solutions are becoming smarter, analyzing user behavior, location, and device information to dynamically adjust access levels. This trend enhances security by tailoring permissions to the specific context of each access attempt.
Integration with DevOps: IAM is aligning with the principles of DevOps to ensure that security is seamlessly integrated into the development process. DevSecOps, the integration of security practices into DevOps workflows, is a growing trend in the IAM landscape. This approach ensures that security is not an afterthought but an integral part of the development lifecycle.
Continuous Monitoring and Threat Intelligence: Continuous monitoring and integration with threat intelligence are becoming essential components of IAM strategies. Real-time monitoring allows for immediate detection of suspicious activities, while threat intelligence integration ensures that IAM systems are well-informed about emerging cyber threats, enabling proactive defense measures.
Cloud Identity and Access Management: The transition to cloud-based infrastructures has prompted a shift in IAM towards Cloud Identity and Access Management solutions. These solutions offer secure and seamless access to cloud resources, reflecting the contemporary trend of organizations embracing cloud technologies for enhanced scalability and flexibility.
Privacy-Preserving Technologies: Privacy is a growing concern in the IAM landscape, leading to the adoption of privacy-preserving technologies. Techniques like homomorphic encryption and federated identity management allow organizations to maintain strong security measures while respecting user privacy, a trend driven by evolving data protection regulations.
IAM as a Service (IDaaS): IAM as a Service is gaining traction, allowing organizations to leverage IAM functionalities without the need for extensive in-house infrastructure. IDaaS provides a scalable and cost-effective solution, enabling businesses to adapt to evolving security needs without compromising on efficiency.
Conclusion: Securing the cyber gates through effective Identity and Access Management is an ongoing challenge, but the landscape is evolving to meet the demands of a dynamic digital environment. The trends discussed underscore the industry's commitment to innovation, adaptability, and a proactive approach to cybersecurity. As organizations navigate the complexities of modern threats, IAM stands as a formidable ally, continuously fortifying the cyber gates and ensuring that only authorized individuals gain access to the digital kingdom.
- Whats New
- Shopping
- Wellness
- Sports
- Theater
- Religion
- Party
- Networking
- Music
- Literature
- Art
- Health
- Juegos
- Food
- Drinks
- Fitness
- Gardening
- Dance
- Causes
- Film
- Crafts
- Other/General
- Cricket
- Grooming
- Technology

